Webinar: Defend the Digital Dock
Stop Wireless Threats Before They Sink You
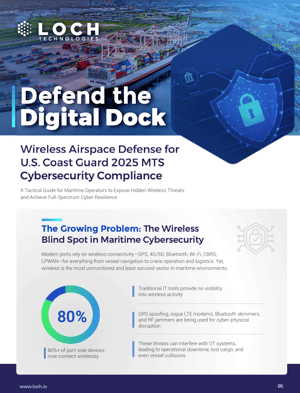
This essential resource dives deeper into the core threats and compliance requirements maritime organizations face, complementing the live discussion with tactical, take-home insights.
-
The hidden risks of wireless blind spots in port cybersecurity
-
A breakdown of the U.S. Coast Guard’s 33 CFR 106 rule and what’s at stake
-
A side-by-side comparison of traditional IT tools vs. LOCH’s RF threat detection
-
How to achieve full-spectrum cyber visibility across maritime infrastructure
-
Practical steps to prepare for 2025 compliance deadlines

Garry Drummond
CEO of LOCH Technologies
Garry Drummond is a seasoned technology executive and author, known for pioneering digital innovation across multiple industries. With a career spanning over two decades, Garry has led transformative initiatives in maritime logistics, cybersecurity, and AI-driven infrastructure. He brings a strategic vision rooted in operational excellence and a passion for leveraging technology to solve complex global challenges. Garry’s insights continue to shape the future of maritime tech through both executive leadership and thought-provoking publications.

Davin Garcia
IT Security, Port of Stockton
Davin Garcia is an IT professional focused on solving complex business challenges through comprehensive technology solutions. With a hands-on, learning-driven approach, Davin continuously evolves his expertise to bridge the gap between business needs and effective technical implementations. His work reflects a deep commitment to improving systems, streamlining processes, and driving impact through thoughtful, scalable innovation.

Benjamin Huey
CTO Innocuous
Benjamin Huey is a seasoned cybersecurity expert with over 30 years of experience in information security and ethical hacking. He has served federal agencies, the U.S. military, the Department of Defense, and numerous Fortune 100 companies. Benjamin brings deep technical expertise across secure infrastructure, cyber warfare simulation, and wireless RF technologies. As a “white hat” hacker, he has led hundreds of offensive security campaigns to help organizations identify vulnerabilities and fortify their defenses against world-class threats.
